Using DUO with AutoElevate
Learn how to use DUO two-factor authentication in conjunction with AutoElevate.
Table of Contents
DUO with Elevations
AutoElevate and DUO can provide multi-factor authentication (MFA) and approval for elevation requests on Windows systems. Here are instructions for using these tools together to ensure secure access to elevated privileges without conflict:
- When installing AutoElevate, DUO is not required for elevations. With AutoElevate, the request is MFA-approved from the AE admin portal side, as MFA is required to log in.
- If installing AutoElevate with DUO, it's recommended that you reinstall DUO with UAC level 0. This ensures that DUO does not interfere with User Account Control (UAC) or elevation requests.
- DUO offers three UAC levels:
- UAC level 0: This level is recommended for use with AutoElevate. It's Windows login only and does not affect UAC or elevation.
- UAC level 1: This level is elevation-only and does not require MFA processing on Windows login. It's not recommended for use with AutoElevate, as it can cause conflicts with the elevation approval process.
- UAC level 2 requires MFA processing on Windows login and UAC prompts. It's not recommended for use with AutoElevate, as it can cause conflicts with the elevation approval process.
- UAC level 0: This level is recommended for use with AutoElevate. It's Windows login only and does not affect UAC or elevation.
- When installing AutoElevate with DUO and using DUO with UAC level 0, there are no admin users to elevate except the AE local ~0000AEAdmin user. This “over-the-shoulder” account is not an admin at rest, so it cannot be used to elevate privileges outside of the AutoElevate process.
- Additionally, you will not need to exclude the AE local ~0000AEAdmin user from the DUO policy, as DUO doesn’t interfere with UAC or elevations in this configuration. Since you're not logging in interactively as the AE admin user, you have a more streamlined and secure process for elevating privileges
More information regarding configuring DUO UAC settings can be found here.
DUO with Admin Login
Requirement
Admin rights are required to run this registry command.
To prevent DUO from blocking the Admin Login credential provider (which is needed for Admin Login to function), you must add its GUID to the DUO "ProvidersWhitelist".
The following command will add the GUID of the Admin Login credential provider to the DUO whitelist:
reg add "HKLM\SOFTWARE\Duo Security\DuoCredProv" /v ProvidersWhitelist /t REG_MULTI_SZ /d "{00006D50-0000-0000-B090-00006B0B0000}" /fThe GUID of the Admin Login credential provider is: 00006D50-0000-0000-B090-00006B0B0000
For more detailed information and assistance, you can refer to this support article from DUO: https://help.duo.com/s/article/4041?language=en_US
DUO with SSO Integration
AutoElevate/SSO integration in conjunction with DUO MFA is not supported when MFA is delegated to Microsoft Azure, even with conditional access.
"Microsoft does not evaluate authentication with a custom control as part of a Conditional Access multifactor authentication claim requirement. Custom controls, like the Duo custom control for Azure CA, cannot satisfy a CA rule that requires “multifactor.” from the Duo support document located here: Duo Two-Factor Authentication for Microsoft Azure Active Directory | Duo Security
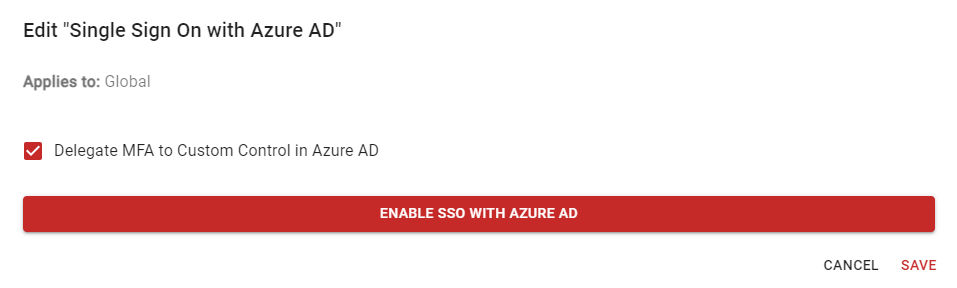
To support AutoElevate/SSO integration with DUO MFA, you will need to delegate MFA to Custom Control in Azure AD Agreement. To enable this option, follow these steps:
- From the Settings screen in the AE Admin Portal https://msp.autoelevate.com, you will need to edit the Single Sign On option (pencil icon).
- Check the Delegate MFA to Custom Control in Azure AD option.
-
Read terms, confirm and then SAVE.